Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News

Radio Frequency: An Airbone Threat to Corporate and Government Networks | 2020-07-06 | Security Magazine

SPACEX - 5G - Earth in Microwave Oven - Satellites - Frequencies from 10.7 GHz to 86 GHz - Directed Energy Weapons - Palpitations - Abnormality of the Heartbeat - Stop 5G

White House staying quiet on reports of mysterious 'radio frequency' attacks making people sick | Newshub



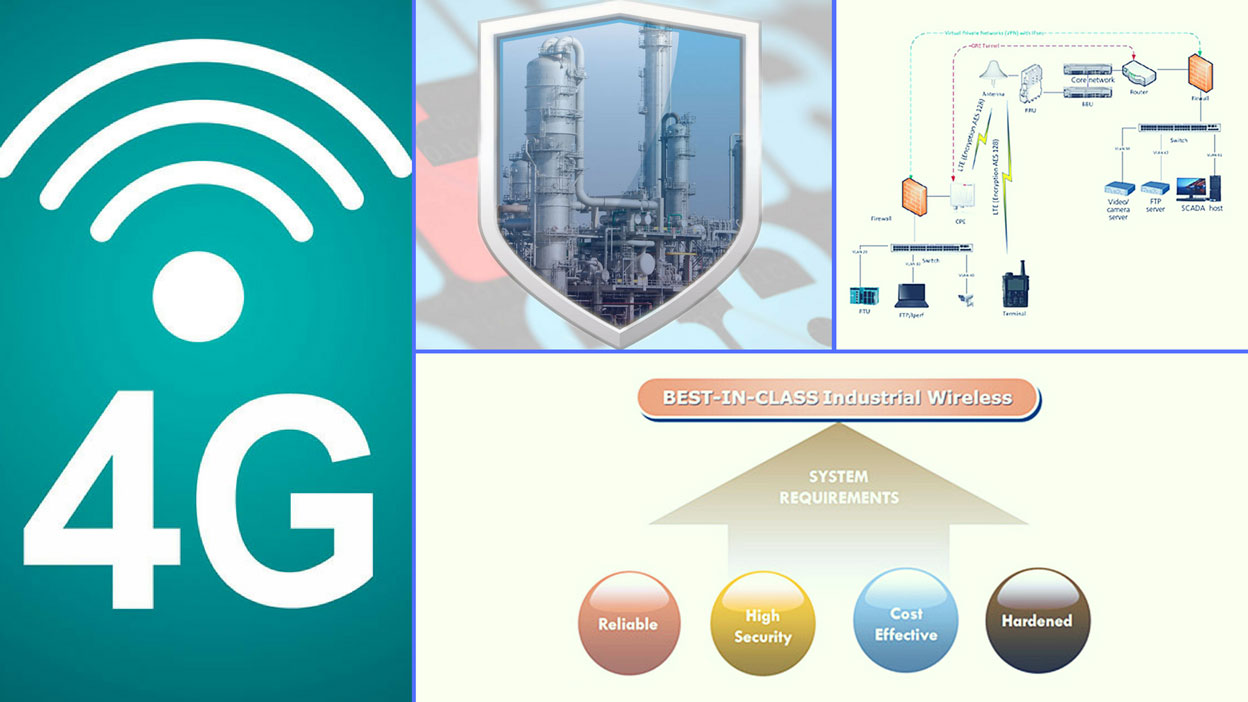





_637280703542341277.png)